Friendly Computers discovered information about a frightening new piece of malware affecting Skype users, which records your voice calls and could potentially send them to a third party. Read more below…
TrendLabs researchers were alerted of a newly released Proof-of-Concept (PoC) that listens and records voice calls carried out via Skype. Trend Micro detects this as TROJ_SPAYKE.C. Skype is a popular application used for making voice over IP (VoIP) calls.
Upon execution, the DLL component (also detected as TROJ_SPAYKE.C) intercepts Skype traffic and hooks the send and recv APIs. This is done before Skype encrypts the traffic it sends to other users. This enables the Trojan to save all gathered information as audio files, which could then be sent to a malicious user. Here’s a screenshot of the captured information:
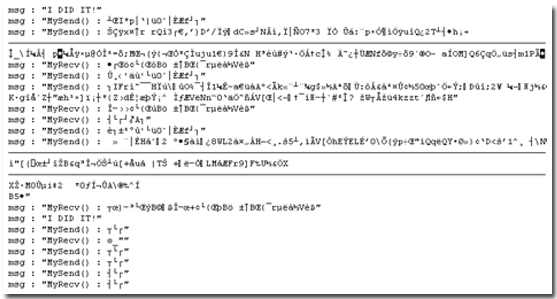
Figure 1. Sample of intercepted trafficThis poses no threat as of the moment; it only collects information but does not decrypt the said information and consequently send it to a remote user. However, future attacks that do engage in information theft cannot be ruled out.
Users are advised not to give away any crucial information when conversing online to prevent info theft. Trend Micro protects users from this attack through the Trend Micro Smart Protection Network.
Source: http://blog.trendmicro.com/trojan-targets-skype-users/


